Information Security Policy Quick Reference Guide to Data Classification and Secure Data Handling - IT Help

TEMPLATE Information Security Awareness and Training Policy | PDF | National Institute Of Standards And Technology | Information Security
9 policies and procedures you need to know about if you're starting a new security program | CSO Online


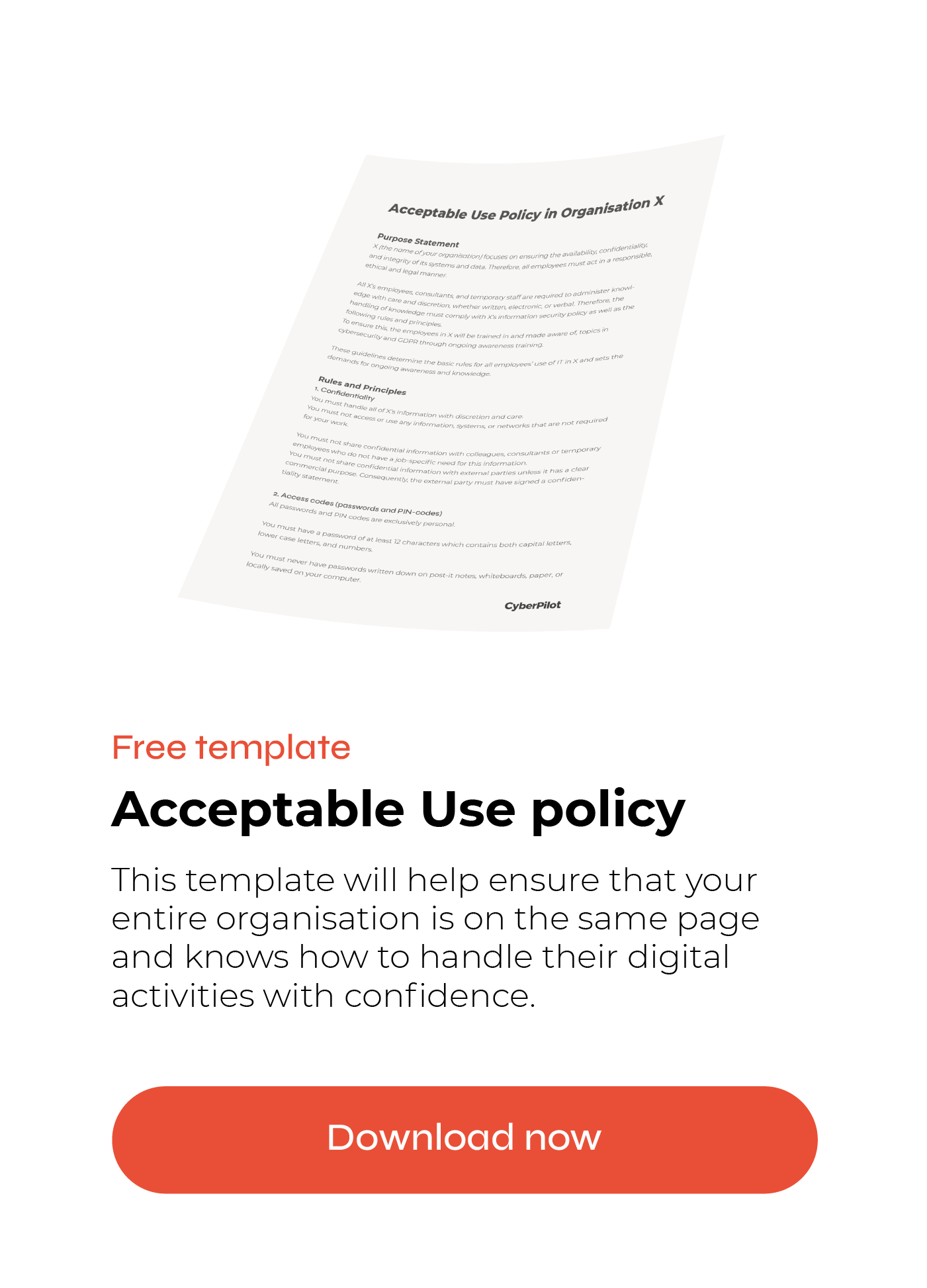






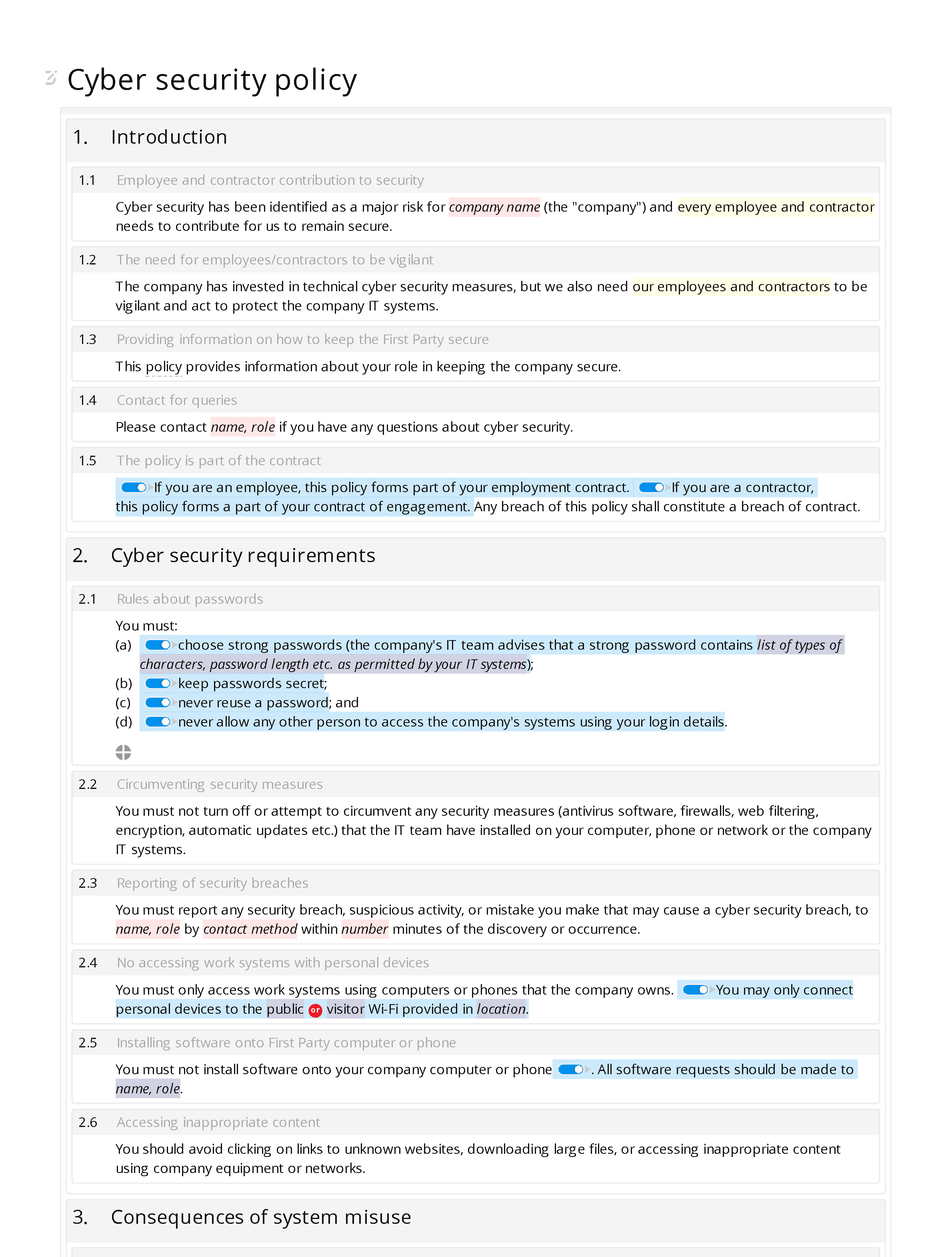
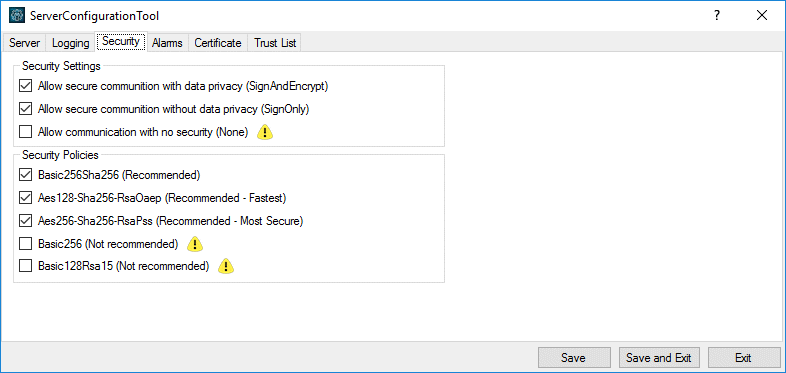

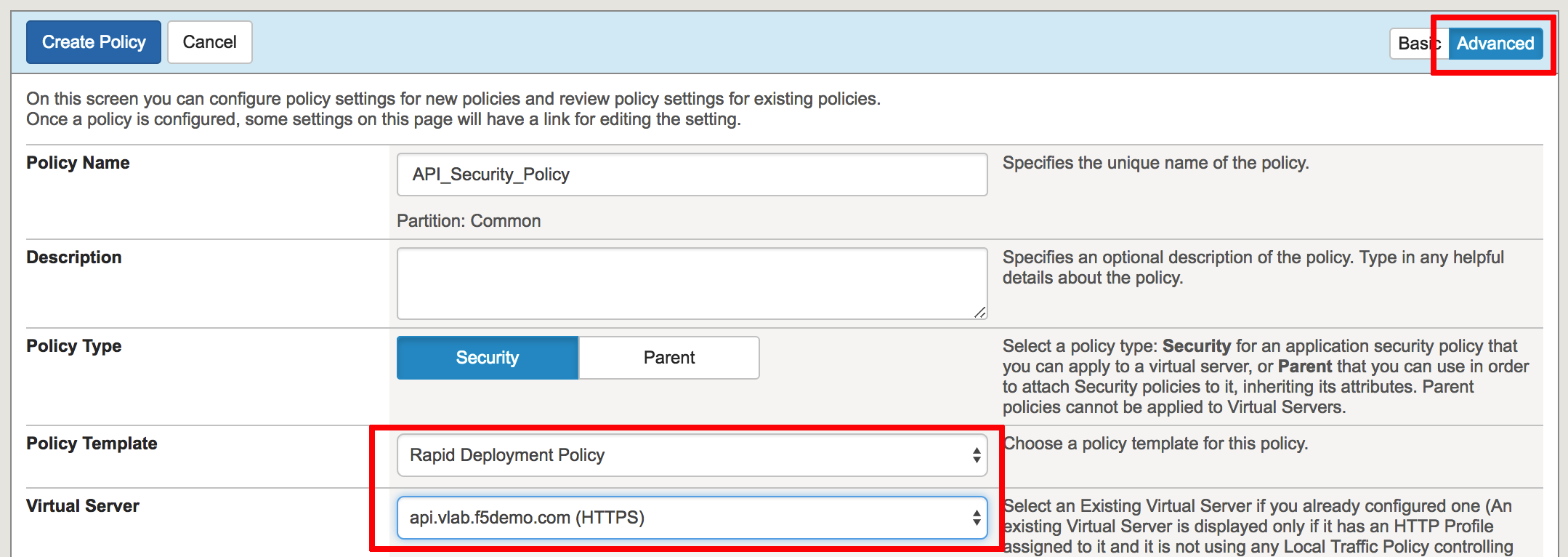








![PDF] Information Security Awareness: Baseline Education and Certification | Semantic Scholar PDF] Information Security Awareness: Baseline Education and Certification | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1ae7c8a22446d973fee316a914220fc4906dcf2b/9-Figure1-1.png)